Articles
WAF vs Firewall
Confused about the differences between a WAF and a firewall? Find out the key differences between these two crucial cyber security measures for business.

ZTNA or Zero Trust Network Access
Get up to speed with the importance of ZTNA (Zero Trust Network Access) and why it’s a more secure way to protect corporate security & data. Learn more here!

SASE or Secure Access Service Edge
Get an overview of the features and benefits of SASE (Secure Access Service Edge) technology and learn how it can help you secure your remote workforce.

Stateful Packet Inspection (SPI) Firewall
Learn more about stateful firewall technology and how it can enhance your network security, protect against malicious attacks, and reduce false positives.

Intrusion Detection and Prevention Systems
Keep your information safe with an intrusion detection and prevention system. Learn the basics of how it works and why you need one for your digital assets.

Cyber Security for Business
Explore cyber security for business and the crucial role of all-encompassing cyber security solutions in defending enterprises against cyber threats.

Fortinet Security Fabric
Fortinet Security Fabric comprises several components that work together to provide an integrated security framework. Let’s explore their main components.

Fortinet Training
From fortifying defense capabilities to enhancing operational efficiency, Fortinet training equips cyber security professionals with the knowledge needed.

AntiSpam
Spam is any unsolicited message that is sent to a large number of recipients and there are many types of spam. Learn more about the importance of anti-spam.

Ransomware Attack
Ransomware is devastating causing business downtime, damage to brand reputation, loss of sensitive data and financial losses. Learn more about the attack.

Function of Firewall
Firewalls are an essential component of network security and have developed over the years to protect against unauthorized access to data and systems.

EDR or Endpoint Detection and Response
Endpoint Detection and Response (EDR) is the technique and tool used to keep track of endpoint activities, spot risks, and thwart cyber attacks.

Brute Force Attack
In a brute force attack, usernames and passwords are ‘guessed’ to log into a system. 5% of security breaches were caused by brute force attacks.

Unified Threat Management
A system of information security known as Unified Threat Management (UTM) offers a single point of defense against cyber threats and network attacks.

Software Firewall
Software firewall is a firewall program that is installed on a computer or server. Learn more about its pros & cons for businesses in Malaysia.

Network Security
Regardless of size, industry, or infrastructure, every organization needs network security solutions to protect it from threats & vulnerabilities.

SD WAN vs MPLS
SD-WAN is a virtual overlay separated from physical lines while MPLS is a dedicated circuit. Learn more about the key distinctions between them.

Firewall Security
Firewall security protects the network from malicious traffic at set boundary levels. Learn more about the different types and deployments available.

SIEM or Security Information and Event Management
SIEM is software that combines security information management and security event management to improve security awareness in IT.

Cybersecurity Threat
Since the dot-com boom in the late 1990s, cybersecurity has been a top issue in the world and also one of Malaysia’s top concerns.
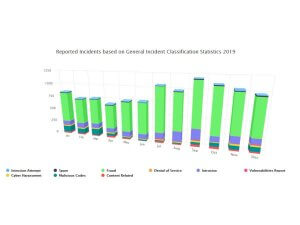
Cyber Crime in Malaysia
Nearly 70% of all business crime cases in Malaysia are now classified as cybercrime. Read more about the cyber crime cases in recent years.

Cybersecurity
The practice of deploying people, rules, and technologies protecting cyber assets is known as cybersecurity. Learn more about its importance.

Web Security
Web security is the process of protecting websites from vulnerabilities. Learn more about the technologies of and threats to web security.

Application Security
Application security is the process of putting security measures into applications. Learn more about the vulnerabilities and tests involved.
Endpoint Security
Endpoint security & protection is the critical last line of defense against cyber attacks. It protects end-user devices like laptops, smartphones, or tablets.

Hardware Firewall
Hardware firewall strengthens your first-line of security defense against cyber threats. It acts as a protective barrier between your network & the internet.

Preventing Ransomware in Small Businesses
Hackers Are Attacking Small Businesses with Ransomware Ransomware is when hackers gain access into an organization’s network, usually via malicious email, and demand payment of
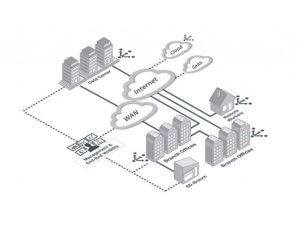
SDWAN or Software Defined Wide Area Network
SDWAN or Software Defined Wide Area Network provides more security & reduces disruption for persistent connection. It empowers your workforce to work remotely.
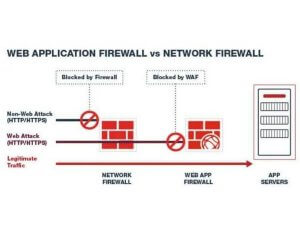
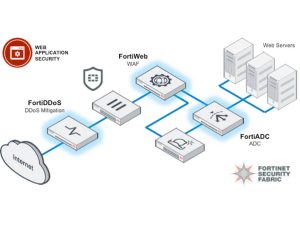
WAF or Web Application Firewall
WAF or Web application firewall protects web applications against emerging cyber threats. It works by targeting Hypertext Transfer Protocol (HTTP) traffic.

NGFW or Next Generation Firewall
Next gen firewall (NGFW) such as FortiGate has capabilities beyond a traditional firewall. It is the 3rd generation & current standard for firewall technology.