In today’s rapidly evolving digital landscape, cyberspace is becoming increasingly complex, volatile, and dangerous.
Businesses and individuals alike face escalating security threats from state-sponsored actors, hacktivist groups, insider risks, human errors, and malicious cybercriminals.
To combat these challenges, organizations of all sizes are racing to implement advanced endpoint security solutions designed to address the ever-growing wave of modern cybersecurity threats.
What is endpoint security?
Endpoint security provides administrators and IT professionals with advanced tools that harness cloud computing, and artificial intelligence (AI) to combat today’s sophisticated security threats.
These solutions continuously monitor network and system activities, providing the investigation and remediation capabilities needed to respond to dynamic security incidents and alerts.
What is considered an endpoint?
Endpoints refer to any external device that connects to an organization’s internal network and systems.
This includes desktop computers, laptops, mobile devices, Internet of things (IoT) devices, tablets, point-of-sale (POS) systems, servers, and other IT equipment.
Interestingly, devices running digital security solutions designed to protect these physical devices are also commonly called endpoints.
How it works?
Endpoint security solutions swiftly block any suspicious behavior or files engaging in malicious activities, effectively reducing risks.
Powered by advanced security tools, these solutions leverage behavioral heuristics to analyze files and executables in real-time.
By doing so, they proactively and predictively neutralize threats before they can cause harm.
What are the characteristics of endpoint security solutions?
Key features of endpoint security solutions include:
- Real-Time Threat Detection and Response: A good endpoint security tool monitors threats and responds quickly to attacks, keeping your systems secure.
- Comprehensive Threat Protection: Protect against malware, ransomware, and zero-day exploits with reliable, all-around defense.
- Scalability for Growing Businesses: Your security solution should grow with your business, scaling easily without losing performance.
- Cross-Device Flexibility: Effective endpoint security works across desktops, laptops, servers, and mobile devices, providing consistent protection everywhere.
- User-Friendly Management: Endpoint security should be easy to deploy and manage, with intuitive interfaces for hassle-free administration.
What are endpoint attacks?
Endpoint attacks target the devices that serve as entry points to a network, including smartphones, computers, laptops, tablets, servers, workstations, and Internet-of-Things (IoT) devices.
These endpoints are prime targets for attackers to execute malicious code, exploit vulnerabilities, and access valuable assets.
From encrypting data to exfiltrating sensitive information or leveraging devices for further attacks, endpoints are at the frontlines of cybersecurity threats.
Why endpoint security is important?

The rapid pace of digital transformation and technological advancements has led to an explosion in the number of devices being manufactured and connected to networks.
While this connectivity drives innovation, it also creates countless opportunities for cybercriminals to exploit vulnerable and poorly protected endpoints.
Every second, over 127 IoT devices connect to the internet, and in 2020, nearly half of all security breaches globally were linked to endpoint security failures.
In today’s digital landscape, securing endpoints has become a critical priority.
Even small security vulnerabilities are actively targeted by cybercriminals, underscoring the need for robust endpoint security.
Businesses are increasingly recognizing the importance of safeguarding their critical systems, sensitive data, and overall infrastructure.
Those that fail to implement adequate endpoint security measures face severe consequences.
Potential losses average $7.12 million—or $440 per compromised endpoint—depending on the scope and severity of the attack.
The repercussions of endpoint breaches can be devastating, often resulting in operational disruptions, significant data loss, and a sharp decline in revenue.
Endpoint Security vs Antivirus
The key distinction between antivirus software and endpoint security lies in the scope of protection.
Antivirus is designed to protect a single device by being installed directly on it, whereas endpoint security protects an entire network, including all connected endpoint devices and operating systems.
Additionally, there are several other differences, which are outlined below:
Antivirus | Endpoint Security | |||
Device coverage | One (1) endpoint device. | All endpoint devices are connected to the enterprise network. | ||
Protection from threats | Against known threats in the businesses’ database. | Against data loss, fileless and signatureless malware, and phishing attacks in addition to protection against known threats. | ||
Continuous protection | The update is done by the user which puts the endpoint device at risk if the antivirus program is not updated. | Connected to the cloud and update is done automatically ensuring users have the latest version. | ||
Advanced internal protection | Protection against malware only but not to internal users own action like stealing data using removable storage devices. | Protection against malware and data leakage by internal users with features like data encryption and data access controls. | ||
Admin control | Relies on users and puts the endpoint device at risk if the antivirus program is not updated. | Provides interconnected security that allows admin control by the IT security team and reduces the risk of human error. | ||
Enterprise wide control | Notifies threats detection to users only then the threats will be investigated by the IT security team. | Centrally managed security solutions that allow admins to monitor, investigate, configure, patch, and resolve any security issues remotely. | ||
Integration | Operates as a single program. | Offers integration with various security solutions within a suite for better endpoints protection. |
Best Endpoint Security Solution: Fortinet FortiClient
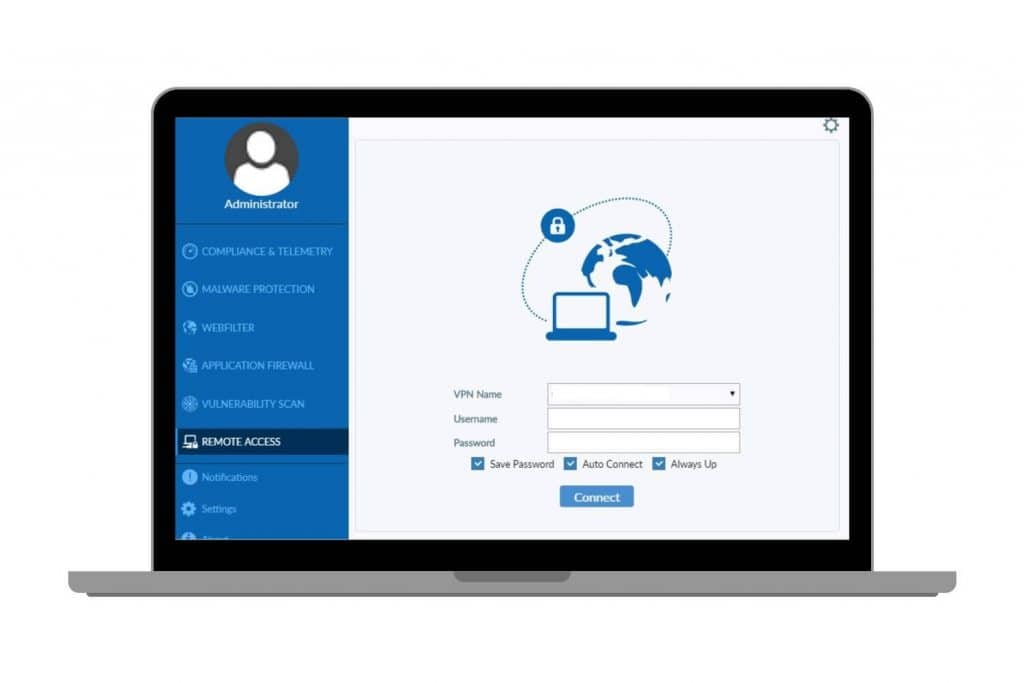
Image via fortinet.com
FortiClient is an advanced security solution designed to safeguard your data and assets from sophisticated threats.
It offers robust features such as deep scanning, threat investigation, and automated remediation to detect and neutralize infections before they can cause harm.
With heuristic monitoring, FortiClient identifies suspicious behavior across endpoints, IoT devices, and web traffic, ensuring comprehensive network protection.
Additionally, FortiClient enhances endpoint hygiene and strengthens defenses to minimize your attack surface, allowing you to focus on what matters most.
As a leading endpoint security software, it provides end-to-end protection, compliance support, and secure access features to keep your data and devices safe.
ZTNA Edition
FortiClient’s ZTNA Edition provides secure access to internal applications without traditional VPNs, following the “least privilege” principle to limit exposure.
It uses advanced security features like TLS encryption, two-factor authentication, and micro-segmentation.
Additionally, it includes tools like user behavior analytics and Endpoint Detection and Response (EDR) for enhanced threat detection and proactive defense.
EPP/APT Edition
FortiClient’s EPP/APT Edition delivers advanced endpoint security with features like sandboxing, behavioral analysis, and AI-driven malware detection.
It also offers vulnerability management, application control, and web filtering to protect against cyber threats. A centralized management console simplifies security operations across the organization.
FortiClient EMS
FortiClient EMS provides centralized control over endpoint devices, ensuring compliance with security standards through efficient management of updates, patches, and policies.
Scalable for organizations of any size, it secures thousands of endpoints against cyber threats while offering real-time reporting and analytics for proactive threat detection and response.
FortiClient VPN
FortiClient VPN secures remote access by protecting data and communications from cyber threats using SSL and IPSec protocols.
It offers advanced monitoring, compliance reporting, and scalability for businesses of all sizes, delivering reliable and adaptable network security.
Get Started With the Right Endpoint Security Solution

Deploying a robust endpoint security solution like FortiClient from Fortinet Malaysia provides reliable protection for your endpoints.
It also ensures comprehensive security for your data, networks, IT infrastructure, and critical systems.
The level of protection your organization requires will depend on your unique security needs and long-term objectives.
At Spectrum Edge, we provide industry-leading solutions like FortiClient, equipped with all-in-one security tools to safeguard your business and IT infrastructure.
Contact us today to strengthen your defenses with cutting-edge endpoint security strategy.