Image via fortinet.com
With the rise of sophisticated cyber threats, relying only on reactive security measures is inadequate.
Intrusion Prevention Systems (IPS) provide a proactive defense for maintaining the security of digital infrastructures in today’s interconnected world.
What is an Intrusion Prevention System?
An Intrusion Prevention System (IPS) is a network security tool that detects and prevents threats in real-time by actively monitoring network traffic.
It uses techniques like signature-based detection, anomaly detection, and stateful protocol analysis to identify potential threats.
Once detected, the IPS can block malicious traffic, reset connections, or alert administrators, enhancing network security and protecting against cyber threats like malware and unauthorized access.
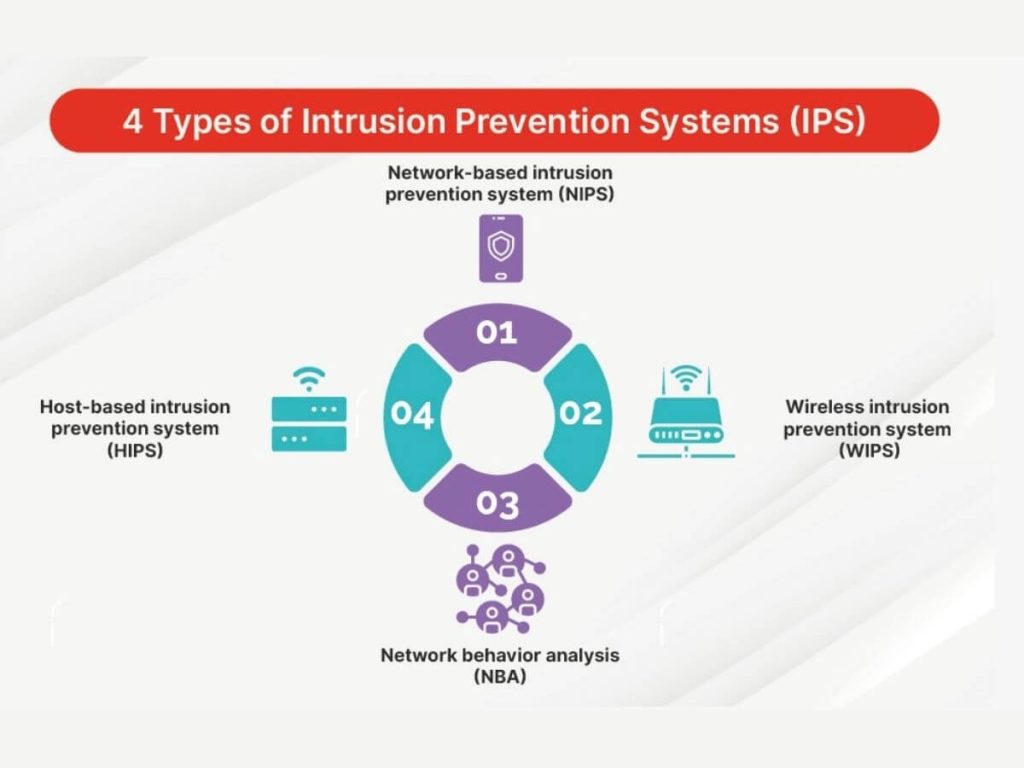
Types of Intrusion Prevention Systems
- Network-based Intrusion Prevention System (NIPS) examines network traffic in real time, often deployed at gateways or access points. They detect and block malicious activities, like DDoS attacks, by analyzing unusual traffic flows and signatures, ensuring the security and integrity of an organization’s network infrastructure.
- Host-based Intrusion Prevention Systems (HIPS) are installed on individual devices to shield them from threats by continuously monitoring system activities and behaviors. They detect suspicious actions, such as system calls and file modifications, and can take immediate action like blocking traffic. HIPS are crucial for securing critical endpoints and keeping devices safe.
- Wireless Intrusion Prevention Systems (WIPS) enhance security for Wi-Fi networks by detecting and preventing unauthorized access and malicious activities. They monitor wireless traffic, detect rogue access points, and block unauthorized devices. By scanning the wireless spectrum, WIPS can identify and mitigate threats like man-in-the-middle attacks, ensuring the confidentiality and integrity of wireless communications.
- Network Behavior Analysis (NBA) Systems monitor network traffic to detect unusual activities that might signal a security threat. Unlike traditional IPS, which depend on known signatures, NBA uses behavioral analytics to find anomalies, enabling it to detect unknown or zero-day threats. By analyzing normal network behavior and spotting deviations, NBA systems can provide early warnings and take proactive steps against potential attacks. This makes them essential for identifying sophisticated threats that traditional methods might miss.
What does an IPS do when it detects an attack?
Image via fortinet.com
When an IPS detects a potential threat, it takes immediate action to prevent further damage. Depending on the type of IPS and its configuration, it can take one or more of the following actions
Detecting Attacks
An IPS monitors network traffic to identify threats by analyzing data packets for anomalies or known malicious signatures. It uses signature-based detection, anomaly detection, and stateful protocol analysis to detect suspicious behavior.
Monitoring Traffic Patterns
An IPS monitors network traffic to establish normal behavior and detect anomalies that indicate potential attacks, such as traffic spikes or unusual logins. It uses advanced machine learning to improve detection of evolving cyber threats.
Response Actions
- Blocking Malicious IP Addresses or Traffic: IPS blocks malicious IP traffic to stop attacks at their source.
- Dropping or Rerouting Suspicious Packets: IPS can drop suspicious data packets to stop threats or reroute them for further analysis to minimize damage.
- Sending Alerts to Security Administrators: IPS automatically acts on detected threats and alerts security administrators with attack details, affected systems, and remediation steps for quick response.
Intrusion Detection System vs Intrusion Prevention System
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are crucial for network and data security, each serving unique roles and employing different strategies to manage threats.
Proactive Approach of an IPS
An Intrusion Prevention System (IPS) not only detects but also blocks threats in real-time.
Unlike Intrusion Detection Systems (IDS), such as Network Intrusion Detection Systems or Host Intrusion Detection Systems, an IPS actively neutralizes threats by blocking harmful IPs and suspicious packets.
This proactive defense helps prevent cyberattack damage.
Integration of IDS and IPS in Modern Cybersecurity
- Complementary Functions: An IDS detects and alerts about threats, while an IPS can actively block them. Combining both provides comprehensive threat detection and real-time prevention.
- Layered Defense: Integrating IDS with IPS enhances security by providing a layered defense, where IDS identifies threats the IPS might miss, ensuring no threats are overlooked.
- Enhanced Incident Response: Security teams benefit from the IDS and IPS systems working together. IDS offers detailed alerts and logs, while IPS quickly blocks threats, leading to faster and more efficient incident response.
FortiGate’s Intrusion Prevention System Solutions

Fortinet is a leader in cybersecurity, known for its effective security solutions.
Its FortiGate Intrusion Prevention System (IPS) uses advanced analytics and threat intelligence to detect and prevent cyber threats in real-time, providing robust protection for organizations by continuously monitoring network traffic.
FortiGate IPS showcases Fortinet’s commitment to securing digital infrastructures against evolving cyber threats.
Spectrum Edge, Malaysia’s leading distributor of Fortinet solutions, offers cutting-edge cybersecurity innovations to protect your digital assets.
With extensive expertise, they provide tailored security solutions and ongoing support to ensure seamless integration and maximum protection from cyber threats.
Partner with Spectrum Edge for reliable and advanced cybersecurity measures, safeguarding your business in the modern digital landscape.