Need more information? Contact us at contact@spectrum-edge.com
When controls for physical equipment connect to broader computer networks, the digital attack surface expands, allowing cyberattackers to penetrate industrial organizations in new ways. As a result, breaches are more frequent.
Nearly 9 in 10 organizations using ICS indicate they have experienced a breach in those systems, with nearly 6 in 10 breached in the past year.
Many of those organizations are adding to their risk by allowing partners as well as IT networks a high level of access into their OT systems.
The following are representative examples of how OT environments are attacked and the ensuing damage:
-
German Steel Mill Suffers Massive Damage to Equipment
According to a German government report, a 2014 cyberattack in a German steel mill began when an employee opened a spearphishing email and clicked on a link. Malware downloaded and allowed an attacker to enter the plant’s business network and eventually move to the OT systems controlling the plant. Details about tactics used were not specified. Once in the OT environment, the attacker compromised a “multitude” of systems, showing expertise in industrial controls. “Failures accumulated in individual control components or entire systems,” the report notes. As a result, the plant was “unable to shut down a blast furnace in a regulated manner,” resulting in “massive damage to the system.” Neither attacker nor motive has been discovered to date.
Malware Shuts Down Operations in Major Businesses Globally
In June of 2017, allegedly state-sponsored malware known as NotPetya appeared in Ukraine and raced within hours to countless machines around the world, destroying master boot records in IT systems. It used a Windows vulnerability that many firms had not patched and combined that exploit with one that retrieved credentials out of system memory to break into other, adjacent systems. Together, the two techniques created “the fastest propagating piece of malware we’ve ever seen,” a security researcher told WIRED magazine.19 Before NotPetya was done, it had caused OT shutdowns in a prominent global shipping firm and pharma firm, among others, and triggered an estimated $10 billion in total damage.
-
Trail of Vulnerabilities Leads Attackers to Water Company’s Controls
Administrators at an unnamed water utility noticed there had been unexplained valve and duct movements in its OT environment over the previous 60 days. A Verizon Breach Digest Report called the organization the “Kemuri Water Company” (KWC), and a Verizon team began an investigation.
KWC supplies water to several counties, and some of its PLCs regulate chemicals that make the water safe to drink. They had been manipulated, disrupting flow rate and water service. What exactly had happened? Verizon researchers found a trail of vulnerabilities providing clues: There were IP addresses in KWC’s web application server log that had previously been involved in attacks on other organizations investigated by the Verizon team. KWC had a web-based payment application that did not require two-factor authentication. And from the web application server, a cable ran to an AS400 system that managed the OT environment. On the web server, investigators found an initialization (INI) file in KWC’s payment application that contained the internal IP address and administrative credentials for the AS400 system in clear text. That meant unauthorized access to the payment application could lead directly to sensitive information on the AS400.
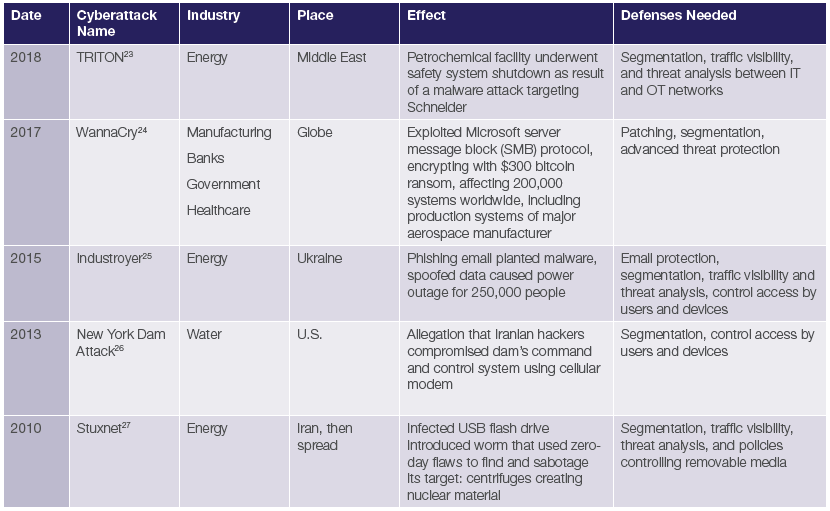
Table: Example of Disclosed CyberAttacks | Source: A Solution Guide to Operational Cybersecurity
Key Takeaways from OT Cyberattacks:
Let’s get in Touch! Contact us now